New
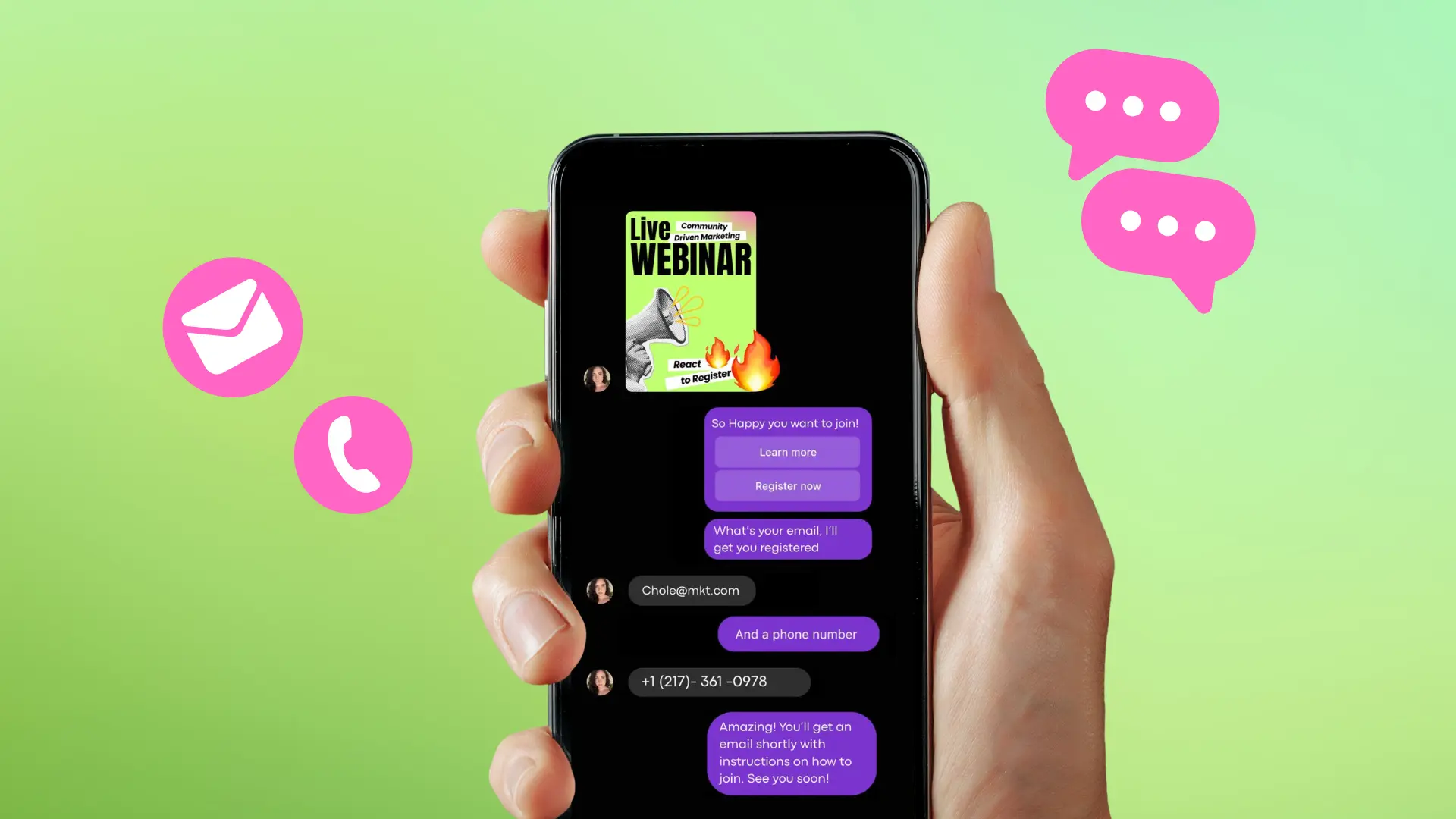
Turn Your DMs Into Lead Gen!
Learn how to collect lead data from your DMs such as email addresses, phone numbers, and more right from your social inbox. If you are not yet automating your DMs your competitors are outpacing you.

How Something Social Saved 75% of Their Time and Increased Revenue by 15%
See how a fast-growing agency improved operations, cut down hours of manual work, and unlocked new revenue opportunities with Vista Social.
New
50 Unique Social Media Ideas for Consistent Content Creation
Discover 50 unique social media post ideas to engage your audience, grow your brand, and maintain a consistent content strategy with ease!
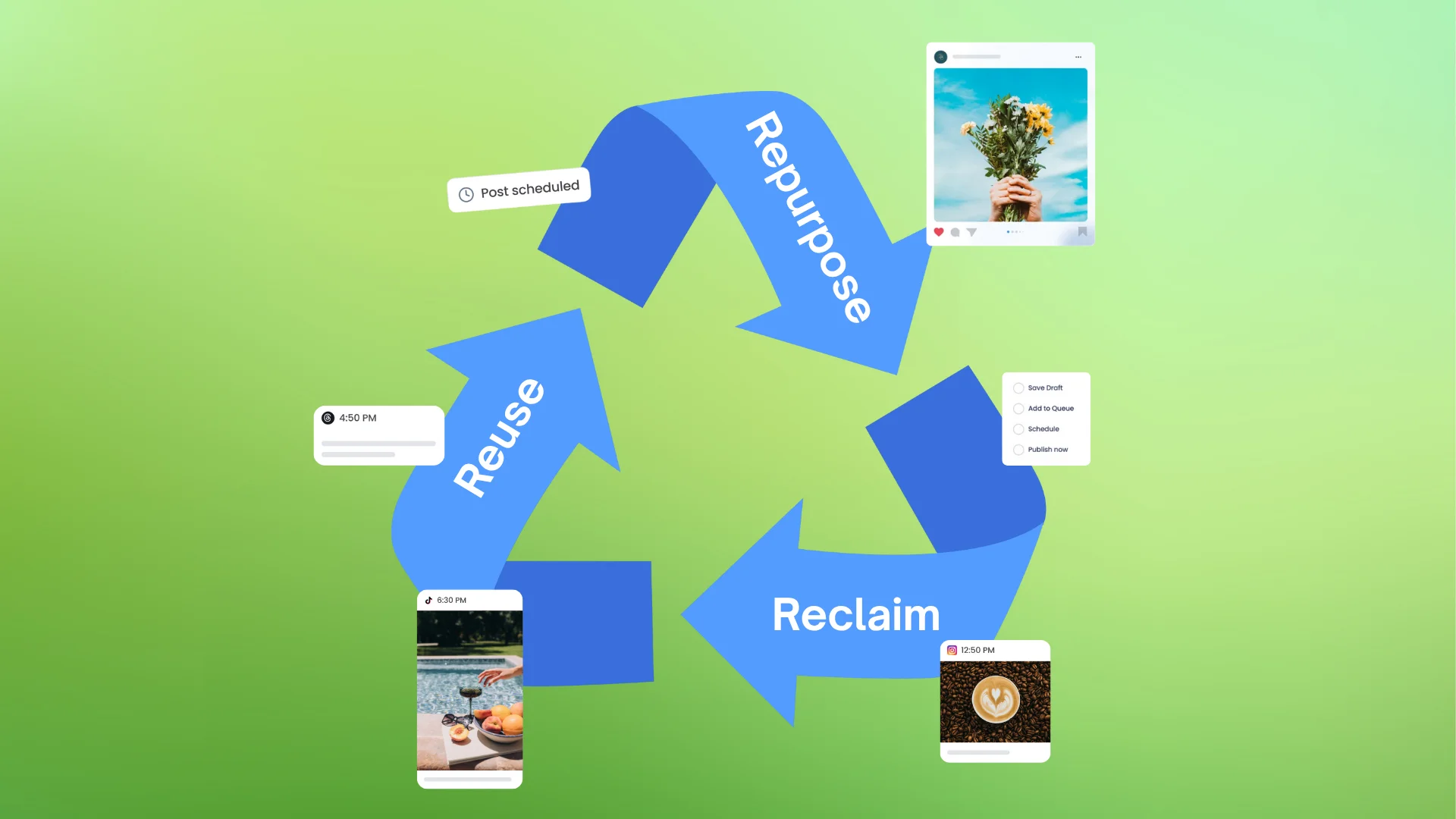
Mastering Content Reuse: The Key to a Consistent and Sustainable Posting Strategy
Security Center
VISTA SOCIAL SECURITY CENTER
In business since 2022, Vista Social has earned the trust of over 30,000 customers who rely on us to manage their social media presence across multiple platforms. Our technology is designed with security, reliability, and privacy at its core. We work daily to build lasting relationships through a culture of transparency, customer success, and unwavering commitment to protecting your data.
This Security Center provides comprehensive information about our security practices, compliance certifications, and operational measures that protect your data and ensure service reliability.
RELIABILITY & AVAILABILITY
Vista Social works hard to minimize impacts and downtime. We design and build our systems and applications for fault tolerance, and our team is trained for fast incident recovery. Vista Social attempts to avoid downtime at all costs, unplanned or planned. Our maintenance efforts, for the most part, require no downtime, except for most unavoidable situations which are quite rare. Business continuity and disaster recovery processes are built into our practices and our systems.
- A proven track-record: 99.99% uptime is a key performance indicator (KPI) for our Engineering group. At the time of writing, we have had higher than 99.95% uptime over the prior 12 months.
- Isolation: Our highly distributed system uses isolation design patterns to mitigate risks across components. Failures of one system component almost never affect other components.
- Transparency to customers: Trust begins with open communication. We publicly share real-time system status and metrics on our status page, https://vistasocial.freshstatus.io/. There we communicate incidents and planned maintenance, including any customer impact, and we display system health metrics sourced from independent third-party providers. Customers may subscribe to receive immediate SMS or email notifications of future incidents.
- Recovery point objectives (RPOs): Recovery strategies are designed to provide up-to-date RPOs at low Recovery Time Objectives (RTOs), with older data recovered against longer RTOs. This is consistent with customer expectations, enabling customers to meet the immediate needs of their customers.
- Social media feeds: Our data processing layer combines multiple connections to social network APIs. Being fully approved on social networks like Facebook, X (Twitter), Instagram, LinkedIn, TikTok, Pinterest, YouTube, Threads, Bluesky, and Reddit, Vista Social is able to have higher levels of redundancy and access to their support teams.
- DevOps best practices: Our engineering team practices Infrastructure-as-code, providing correctness, consistency, testability, and speed to recovery. All 24/7/365 on-call team members are empowered to rebuild systems and topologies with full consistency. In the event of system loss, our Engineering team quickly recreates systems by executing the infrastructure code.
- Backups: Backups are taken frequently, encrypted in transit and at rest, and are tested regularly. Backups are kept "off-site" in Amazon S3 which stores files on multiple physical devices in multiple facilities offering 99.999999999% durability and 99.99% availability.
- Monitoring & on-call support: We monitor continuously from around the world, displaying, alerting, and reporting upon our entire technical environment in real-time. Supporting customers is a collaboration between our customer-facing support team and our engineering team. Specialized engineers are on call 24/7/365.
SOCIAL MEDIA INTEGRATIONS
Vista Social integrates with all major social media platforms to provide seamless social media management capabilities.
- Secure connections: All connections between Vista Social and social networks occur over secure, encrypted networks using industry-standard protocols.
- OAuth authentication: When customers connect their social profiles to Vista Social, they authenticate directly on the social network's platform. Vista Social never views, processes, or stores your social network account credentials.
- Platform partnerships: We maintain formal partnerships with major platforms including Facebook, Instagram, X (Twitter), LinkedIn, TikTok, Pinterest, YouTube, Threads, Bluesky, and Reddit, providing us with enhanced API access, priority support, and advance notice of platform changes.
- Redundant connections: Our data ingest layer combines multiple redundant connections to social network APIs, ensuring high availability even if individual API endpoints experience issues.
- Rate limit management: We implement intelligent rate limiting and request throttling to ensure reliable performance and compliance with platform API requirements.
DATA SECURITY
Protecting your data is our highest priority. We implement comprehensive security measures at every layer of our infrastructure.
Encryption
- Data in transit: All data transmitted between your browser and our servers is encrypted using TLS 1.3 with strong cipher suites. API communications use similar encryption standards.
- Data at rest: All customer data stored in our databases is encrypted using AES-256 encryption, the same standard used by financial institutions and government agencies.
- Database encryption: Our MongoDB databases use encrypted storage engines, and sensitive fields are additionally encrypted at the application layer.
- Backup encryption: All backup data is encrypted both in transit and at rest using AES-256 encryption.
Data Storage & Location
- Cloud infrastructure: Vista Social is hosted on Amazon Web Services (AWS), one of the world's most secure and reliable cloud platforms.
- Primary data centers: Our primary production systems are hosted in AWS US-East region (Northern Virginia), with redundancy across multiple availability zones.
- Backup storage: Encrypted backups are stored in geographically separate AWS regions (US-West) to ensure data durability and disaster recovery capability.
- Data residency: Customer data is stored exclusively within the United States, ensuring compliance with US data protection standards.
Data Access Controls
- Principle of least privilege: Access to customer data is restricted to only those employees who require it to perform their job functions.
- Role-based access control: All system access is governed by role-based permissions, regularly reviewed and updated.
- Multi-factor authentication: All employees with access to production systems must use multi-factor authentication.
- Access logging: All access to customer data is logged and regularly audited for security and compliance purposes.
Data Retention & Deletion
- Active data: Customer data is retained for the duration of your account and 30 days following account closure.
- Backup retention: Encrypted backups are retained for 90 days to enable disaster recovery.
- Secure deletion: Upon account termination, customer data is securely deleted from production systems within 30 days and from backups within 90 days.
- Customer data export: Customers can export their data at any time through the application interface.
INFRASTRUCTURE SECURITY
Vista Social's infrastructure is built on industry-leading cloud platforms with multiple layers of security protection.
Cloud Infrastructure
- AWS hosting: Our entire infrastructure runs on Amazon Web Services (AWS), leveraging their world-class security, compliance, and reliability.
- Availability zones: Production systems span multiple AWS availability zones to ensure high availability and fault tolerance.
- Geographic redundancy: Critical systems and backups are distributed across multiple geographic regions.
- Auto-scaling: Infrastructure automatically scales to handle traffic spikes and maintain performance.
Network Security
- Virtual Private Cloud (VPC): All systems run within isolated VPCs with strict network access controls.
- Network segmentation: Production, staging, and development environments are completely segmented.
- Firewall protection: Multiple layers of firewalls protect our infrastructure, with default-deny rules and whitelist-only access.
- DDoS protection: Cloudflare provides enterprise-grade DDoS protection and Web Application Firewall (WAF) capabilities.
- Intrusion detection: Automated intrusion detection systems monitor for suspicious network activity 24/7.
System Hardening
- Minimal attack surface: All servers run minimal software installations with unnecessary services disabled.
- Security updates: Operating systems and software are kept current with the latest security patches through automated update processes.
- Configuration management: Infrastructure-as-code ensures consistent, secure configurations across all systems.
- Bastion hosts: Administrative access to production systems requires connection through hardened bastion hosts with strict access controls.
Monitoring & Logging
- Centralized logging: All system logs are aggregated in a centralized logging system for analysis and alerting.
- Real-time monitoring: Comprehensive monitoring provides real-time visibility into system health, performance, and security.
- Automated alerts: Automated alerting notifies our security and operations teams of potential issues immediately.
- Log retention: Security and access logs are retained for 1 year to support security investigations and compliance.
APPLICATION SECURITY
Security is integrated into every phase of our software development lifecycle.
Secure Development Lifecycle
- Security requirements: Security requirements are defined during the planning phase of all new features.
- Secure coding standards: Developers follow established secure coding guidelines to prevent common vulnerabilities.
- Code review: All code changes undergo peer review before deployment, with security considerations as a key review criterion.
- Automated testing: Comprehensive automated test suites run on every code change to catch security regressions.
Security Testing
- Static analysis: Automated static code analysis tools scan for security vulnerabilities during development.
- Dependency scanning: All third-party dependencies are scanned for known vulnerabilities before use.
- Penetration testing: Independent security firms conduct comprehensive penetration tests quarterly.
- Vulnerability assessments: Regular vulnerability scans identify and prioritize security issues for remediation.
Common Vulnerability Protection
- SQL injection prevention: Parameterized queries and input validation prevent SQL injection attacks.
- XSS protection: Output encoding and Content Security Policy headers protect against cross-site scripting.
- CSRF protection: Anti-CSRF tokens protect against cross-site request forgery attacks.
- Authentication security: Secure session management, password hashing with bcrypt, and protection against brute force attacks.
- API security: Rate limiting, input validation, and OAuth 2.0 authentication protect our APIs.
Dependency Management
- Automated updates: Dependency management tools automatically identify and update vulnerable packages.
- Security advisories: We monitor security advisories for all dependencies and apply patches promptly.
- License compliance: All open-source dependencies are reviewed for license compatibility and security.
ACCESS CONTROL & AUTHENTICATION
Vista Social provides robust access control features to help you manage who can access your accounts and data.
Customer Access Controls
- Two-Factor Authentication (2FA): All accounts can enable 2FA using authenticator apps (TOTP) for enhanced security. We strongly recommend enabling 2FA for all users.
- Single Sign-On (SSO): Enterprise customers can use SSO via SAML 2.0 to centralize authentication and enforce organizational security policies.
- Role-Based Access Control (RBAC): Granular permission controls allow you to assign specific roles and permissions to team members based on their responsibilities.
- Team management: Account administrators can add, remove, and manage team member access with detailed audit trails.
- Session management: Automatic session timeouts and the ability to remotely terminate active sessions enhance security.
Password Security
- Strong password requirements: Passwords must meet minimum complexity requirements including length, character variety, and strength.
- Password hashing: Passwords are hashed using bcrypt with salt, making them computationally infeasible to reverse.
- Breach detection: We check passwords against known compromised password databases to prevent use of exposed credentials.
- Password reset security: Secure password reset flows with time-limited tokens and email verification.
API Security
- API authentication: API access requires authentication tokens with configurable permissions and expiration.
- Rate limiting: API rate limits prevent abuse and ensure fair resource allocation.
- IP whitelisting: Enterprise customers can restrict API access to specific IP addresses.
- OAuth 2.0: Third-party integrations use OAuth 2.0 for secure, delegated authorization.
Audit & Activity Logging
- Activity logs: Comprehensive activity logs track all user actions within the application.
- Login history: Users can view their login history, including timestamps, IP addresses, and device information.
- Change tracking: All changes to account settings, team members, and permissions are logged.
- Export capabilities: Enterprise customers can export activity logs for compliance and security analysis.
PERSONNEL SECURITY
Our employees are our first line of defense in protecting customer data. We invest heavily in security awareness, training, and enforcement.
Security Team
- Dedicated security personnel: Vista Social employs dedicated security professionals responsible for maintaining and improving our security posture.
- Security leadership: Our VP of Engineering provides oversight of all security initiatives, with regular reporting to executive leadership.
- 24/7 coverage: Security team members and on-call engineers provide round-the-clock coverage for security incidents.
Employee Screening
- Background checks: All employees undergo background checks appropriate to their role and location before employment.
- Reference verification: Professional references are verified during the hiring process.
- Identity verification: Identity verification is completed for all employees prior to system access.
Security Training
- Security onboarding: All new employees complete comprehensive security training during onboarding.
- Annual training: All employees participate in annual security awareness training covering data protection, phishing, social engineering, and security best practices.
- Developer training: Engineers receive specialized training on secure coding practices, OWASP Top 10, and security testing.
- Phishing simulations: Regular phishing simulations test employee awareness and provide targeted remediation training.
- Privacy training: All employees receive training on GDPR, CCPA, and other privacy regulations.
Device Security
- Device management: All employee devices are managed through Mobile Device Management (MDM) software.
- Full-disk encryption: All company laptops and workstations use full-disk encryption.
- Endpoint protection: Next-generation antivirus and anti-malware software protects all endpoints.
- Screen lock: Automatic screen locks are enforced on all devices after periods of inactivity.
- USB restrictions: USB ports and external media are restricted on systems with access to production data.
- Remote wipe: Lost or stolen devices can be remotely wiped to prevent data exposure.
Access Reviews
- Regular reviews: Employee access to systems and data is reviewed quarterly.
- Immediate revocation: Access is immediately revoked upon employee separation.
- Least privilege: Employees receive only the minimum access required to perform their job functions.
VULNERABILITY & RISK MANAGEMENT
We take a proactive approach to identifying, assessing, and remediating security vulnerabilities.
Vulnerability Detection
- Continuous scanning: Automated vulnerability scanners continuously assess our infrastructure and applications for security weaknesses.
- Dependency monitoring: All software dependencies are monitored for newly disclosed vulnerabilities.
- Security advisories: We subscribe to security advisory feeds for all technologies in our stack.
- Threat intelligence: External threat intelligence feeds inform our security monitoring and response.
Penetration Testing
- Quarterly testing: Independent security firms conduct comprehensive penetration tests on a quarterly basis.
- Application testing: Testing covers web application security, API security, and authentication mechanisms.
- Infrastructure testing: Network-layer penetration testing assesses our infrastructure security.
- Remediation: All findings are triaged by severity and remediated according to established timelines.
Incident Response
- Incident response plan: We maintain a comprehensive incident response plan based on NIST guidelines.
- Response team: A dedicated incident response team is available 24/7/365 to handle security incidents.
- Response phases: Our process includes preparation, detection, containment, eradication, recovery, and post-incident analysis.
- Customer notification: Affected customers are notified promptly in accordance with legal requirements and our commitment to transparency.
- Continuous improvement: Every incident undergoes post-mortem analysis to prevent recurrence.
Change Management
- Formal SDLC: All changes follow our Software Development Lifecycle with security gates at each phase.
- Code review: All code changes require peer review with security considerations.
- Automated testing: Comprehensive automated tests validate functionality and security before deployment.
- Staged rollouts: Changes are deployed to staging environments before production deployment.
- Rollback capability: All deployments can be quickly rolled back if issues are detected.
Vendor Security
- Vendor assessment: All vendors with access to customer data undergo security assessments.
- Contractual requirements: Vendors must meet security requirements defined in our contracts.
- Regular reviews: Vendor security posture is reviewed annually or upon significant changes.
- Subprocessor transparency: A current list of subprocessors is available to customers upon request.
COMPLIANCE & CERTIFICATIONS
Vista Social is committed to maintaining compliance with industry standards and regulations.
SOC 2 Type II
- Certification status: Vista Social maintains SOC 2 Type II certification, demonstrating our commitment to security, availability, and confidentiality.
- Annual audits: Independent auditors conduct comprehensive SOC 2 audits annually.
- Report availability: SOC 2 reports are available to customers under NDA upon request.
GDPR Compliance
- Data protection: Vista Social complies with the EU General Data Protection Regulation (GDPR) for all customer data.
- Data Processing Addendum: A GDPR-compliant Data Processing Addendum is available at https://vistasocial.com/gdpr/
- Standard Contractual Clauses: We use European Commission-approved Standard Contractual Clauses for international data transfers.
- Data subject rights: We support all GDPR data subject rights including access, rectification, erasure, and portability.
- Privacy by design: Privacy considerations are integrated into all product development.
CCPA Compliance
- California privacy rights: Vista Social complies with the California Consumer Privacy Act (CCPA) and California Privacy Rights Act (CPRA).
- Consumer rights: California residents can exercise rights to know, delete, correct, and opt-out.
- No sale of data: Vista Social does not sell personal information.
- Privacy Policy: Our Privacy Policy details CCPA compliance at https://vistasocial.com/privacy/
Other Compliance
- State privacy laws: We comply with privacy laws in Colorado, Virginia, Connecticut, Utah, and other states with comprehensive privacy legislation.
- CAN-SPAM: Email communications comply with CAN-SPAM Act requirements.
- COPPA: We do not knowingly collect information from children under 13.
Security Frameworks
- NIST Cybersecurity Framework: Our security program aligns with NIST CSF guidelines.
- OWASP: Development follows OWASP secure coding guidelines and addresses OWASP Top 10 vulnerabilities.
- CIS Controls: Infrastructure security implements CIS Critical Security Controls.
PHYSICAL & ENVIRONMENTAL SECURITY
While Vista Social operates in the cloud, we maintain strong physical security for our office facilities and rely on AWS's world-class data center security.
Data Center Security (AWS)
- SOC certification: AWS data centers maintain SOC 1, SOC 2, and SOC 3 certifications.
- Physical access control: Multi-factor authentication, security guards, and biometric scanning protect data center access.
- Environmental controls: Redundant power, cooling, and fire suppression systems ensure continuous operation.
- 24/7 monitoring: AWS security teams monitor data centers around the clock.
- Compliance: AWS maintains compliance with ISO 27001, PCI DSS, FedRAMP, and numerous other standards.
- Physical security details: Learn more at https://aws.amazon.com/compliance/data-center/
Office Security
- Access control: All Vista Social offices use electronic access control systems limiting entry to authorized personnel.
- Visitor management: Visitors must sign in, wear badges, and be escorted by Vista Social employees.
- Surveillance: Security cameras monitor office entry and exit points.
- Secure areas: Network equipment and sensitive systems are housed in locked, access-controlled rooms.
Business Continuity
- Remote-capable operations: Vista Social's operations can continue fully remotely, independent of office availability.
- Distributed workforce: Our team works from various locations, eliminating single points of failure.
- Cloud-native architecture: No dependencies on physical office infrastructure for service delivery.
- Disaster recovery: Geographic redundancy and automated failover ensure service continuity.
TRANSPARENCY & COMMUNICATION
We believe trust is built through transparency. Vista Social is committed to open communication about our security practices and service status.
Status Page
- Real-time status: Our public status page at https://vistasocial.freshstatus.io/ provides real-time system health information.
- Historical uptime: View historical uptime metrics and incident history.
- Incident updates: Detailed updates are posted during incidents, including impact assessment and resolution progress.
- Maintenance notifications: Planned maintenance windows are announced in advance.
- Subscription options: Subscribe to receive SMS or email notifications of incidents and maintenance.
Security Contact
- Security team email: Contact our security team at security@vistasocial.com
- General support: For non-security issues, contact support@vistasocial.com
- Response time: We respond to security inquiries within 24 business hours.
Responsible Disclosure
- Vulnerability reporting: Security researchers and customers can report vulnerabilities to security@vistasocial.com
- Acknowledgment: We acknowledge receipt of vulnerability reports within 24 hours.
- Assessment: Reported vulnerabilities are assessed and prioritized based on severity and impact.
- Remediation: Critical vulnerabilities are addressed immediately; other issues follow risk-based timelines.
- Recognition: We recognize responsible disclosure and may list researchers in our security acknowledgments (with permission).
- No legal action: We will not pursue legal action against researchers who follow responsible disclosure practices.
Security Documentation
- Privacy Policy: https://vistasocial.com/privacy/
- Terms of Service: https://vistasocial.com/terms/
- Data Processing Addendum: https://vistasocial.com/gdpr/
- Acceptable Use Policy: https://vistasocial.com/usage-policy/
- Subprocessor list: Available upon request to enterprise customers
ENTERPRISE SECURITY FEATURES
Vista Social offers additional security features and support for enterprise customers.
Enhanced Access Control
- SAML 2.0 SSO: Centralize authentication through your identity provider (Okta, Azure AD, Google Workspace, etc.)
- SCIM provisioning: Automate user provisioning and de-provisioning
- Advanced RBAC: Custom roles and granular permissions for complex organizational structures
- IP whitelisting: Restrict access to your Vista Social account from specific IP addresses
- Session controls: Configure session timeout policies and concurrent session limits
Advanced Compliance
- SOC 2 reports: Access to SOC 2 Type II reports under NDA
- Custom DPA: Negotiate custom Data Processing Addendum terms
- Security questionnaires: Dedicated support for completing security assessments
- Compliance documentation: Comprehensive security and compliance documentation package
- Audit support: Assistance during your organization's security audits
Enhanced Support
- Dedicated account team: Direct access to account managers and support engineers
- Priority support: Faster response times for technical and security issues
- Security briefings: Regular security updates and briefings for your team
- Custom SLAs: Service level agreements tailored to your requirements
- Incident communication: Direct communication channel for security incidents
Data & Privacy
- Data export: Comprehensive data export capabilities for compliance and portability
- Audit logs: Extended audit log retention and export capabilities
- Data residency: Discussion of data residency requirements and options
- Custom retention: Negotiate custom data retention periods
To learn more about enterprise security features, contact our sales team at sales@vistasocial.com
CONTACT OUR SECURITY TEAM
Have questions about our security practices? Our security team is here to help.
Security Inquiries
Email: security@vistasocial.com
Response time: Within 24 business hours
Vulnerability Reports
Email: security@vistasocial.com
Include: Detailed description, steps to reproduce, and potential impact
Customer Support
Email: support@vistasocial.com
For general product support and non-security questions
Enterprise Sales
Email: sales@vistasocial.com
For enterprise security features and compliance discussions
Additional Resources
- Status Page: https://vistasocial.freshstatus.io/
- Privacy Policy: https://vistasocial.com/privacy/
- Terms of Service: https://vistasocial.com/terms/
- Data Processing Addendum: https://vistasocial.com/gdpr/