New
Turn Your DMs Into Lead Gen!
Learn how to collect lead data from your DMs such as email addresses, phone numbers, and more right from your social inbox. If you are not yet automating your DMs your competitors are outpacing you.

How Something Social Saved 75% of Their Time and Increased Revenue by 15%
See how a fast-growing agency improved operations, cut down hours of manual work, and unlocked new revenue opportunities with Vista Social.
New
50 Unique Social Media Ideas for Consistent Content Creation
Discover 50 unique social media post ideas to engage your audience, grow your brand, and maintain a consistent content strategy with ease!
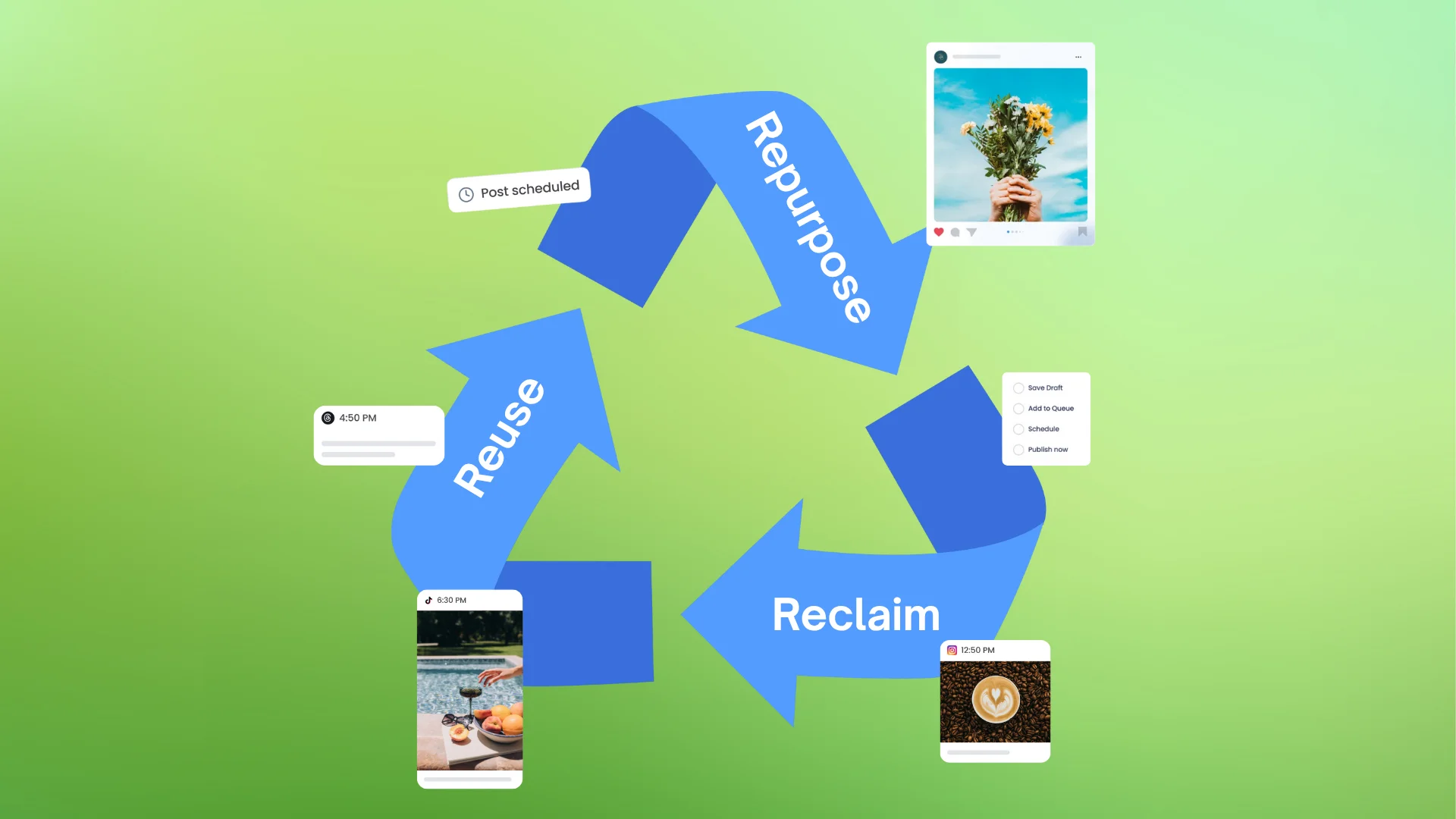
Mastering Content Reuse: The Key to a Consistent and Sustainable Posting Strategy
Published on February 14, 2022
5 min to read
Top 8 Social Media Security Practices to Feel Safe Online
Summarize with AI

Summarize with AI
ChatGPT
Claude
Perplexity
Share
Vista Social
X (Twitter)
Table of contents
Summarize with AI
ChatGPT
Claude
Perplexity
Share
Vista Social
X (Twitter)
With the increased popularity of social media for business communications, safe social networking topic has become highly relevant. The information we share becomes the desired object of fraudulent transactions, blackmail, litigation, and illegal actions for data theft.
Every day the number of attacks on social media accounts is growing. According to the EY Global Information Security Survey 2021, 77% of respondents have seen a clear rise in disruptive attacks over the last year. So, it is critical to consider perspectives for further developing social networks and the evolution of threats associated with them.
Since social media continues to be an essential tool for brand awareness and a top target of hackers, it is worth talking about security best practices to stay safe online.
Table of contents
The Basis of Reliable Security in Social Networks
It is difficult to overestimate the importance of ensuring information security online since storing and sharing corporate data is integral to running any business. And, as with many processes in business, social media security needs a plan, monitoring, and verification.
Documented standards or procedures define approaches to assessing information security and establish requirements to reduce social media security risks. Ensure documenting the following aspects:
- Prepare your standard practices for setting up and maintaining your social business accounts and any other online tools you use.
- Ensure you have details on the distribution of account access to team members.
- Conduct regular audits of those with account access when any changes occur within the team.
- Review security standards with the team members regularly.
It is preferable to have a dedicated team member responsible for social media security. This person will leverage the latest security features and ensure following the best practices within the team. In addition, the social media security manager should cooperate with other security specialists at the company, e.g., security team or IT, in keeping social media accounts secure.
Top 8 Social Media Security Practices
Stay alert.
Whenever you are online, stay vigilant. A team may be careful with the corporate data online, but the attacks on personal accounts with access to company profiles can also influence the brand. Be careful when dealing with suspicious friend requests, opening strange emails, social media messages, and more. Stay alert with links in messages sent on behalf of a social network or another well-known source. Often users inadvertently download malware by clicking on links.
Use strong passwords.
Avoid such universal solutions as a continuous sequence of numbers, lines of simple symbols, letters on the keyboard. Do not use your first name, last name, country of origin as a password, and everything that a potential hacker of your account will first pay attention to. Ideally, the password should contain at least ten characters. It should be a random combination of letters, numbers, and special symbols. There should also be a unique combination for each account. Another way to protect your account is to use an open source password manager that helps you create new login combinations and remember existing one
Secure social media accounts with 2FA/MFA.
Another tool to increase security for a social media account is two-factor authentication or multi-factor authentication. In addition to the password, you will need another login confirmation. Social networks offer several options for such verification: text messages with a code to the cell phone, security codes from a code generator or a third-party application, approval of an attempt to log in from another already recognized device. Most large attacks could be avoided by having a two-factor authentication system on the devices. Today, most social networks have built-in two-factor authentication, which can be enabled in the application settings. Below you can see what the most popular social platforms offer:
- Facebook: Third-party authentication application, SMS code (text message)
- Instagram: Third-party authentication application, SMS code (text message)
- Twitter: Third-party authentication application, SMS code (text message)
- LinkedIn: SMS code (text message)
- Pinterest: SMS code (text message)
- Google My Business and YouTube: Security keys, Google prompt, Google Authenticator, Backup codes, text message, phone call.
Use SSO.
Single Sign-On systems (SSO) are a particular type of product or embedded technology that helps avoid re-authentication of the user when navigating through various sections and services of the same portal or when working with multiple applications. In other words, users go through the authentication procedure in one place, after which they get access to all the related sections and do not have to enter their credentials in several forms. The technology simplifies registering security events related to the identification and authentication procedure — all events are in one place.
Implement social media usage policy.
The social media usage policy gives employees corporate guidelines and principles of communication on the web. This policy can be the first line of the company’s defense, which reduces risks for both the employer and the employee. For example, specify what data cannot be shared, how to respond to sensitive content, and how to manage the risks of direct or indirect reputation damage.
Enhance employees’ information security awareness.
Employees should constantly receive up-to-date information about new Internet threats and ways to avoid the risks. It is also preferable to conduct appropriate training and keep constant contact with team members regarding social media security. It is an essential step in protecting the business from social media phishing attacks.
Establish clear processes to protect against security threats and ensure they are monitored.
Team members in charge must constantly monitor current social media threats. Thus, it is more expedient to establish clear systematic processes related to the daily activities performed by dedicated team members. This seemingly routine process will allow security administrators to detect network attacks in time or avoid them altogether.
Monitor mentions of your brand name and logo on the web.
Brand mentions are references to your company or services on the Internet. This is not only a link to the site but also the brand name, logo, hashtag, or mention in the comments via @. Often scammers hide behind the names of popular brands. Monitoring will help you find fake accounts to report them and save some of the brand’s inattentive audience from a negative experience.
If you are using Vista Social to manage your clients’ social media accounts, you can be sure that strong security measures are available within the platform. Account owners can change user permissions and assign the level of access per entity. Two-step verification, single sign-on, secure credential storage, and access permissions will help to protect social media accounts from security threats.
Conclusion
Social media is an essential tool for modern marketing and branding. However, due to the active use of social networks and the storage of a large amount of confidential data, social media accounts are becoming a popular target for cybercriminals. Therefore, ensure to follow those essential social media security best practices to avoid losing sensitive data, reputation, or data leak.

Get your Vista Social account set up for free to unlock numerous social media management features and stay secure online.
Try Vista Social for free
A social media management platform that actually helps you grow with easy-to-use content planning, scheduling, engagement and analytics tools.
Get Started NowAbout the Author
Content Writer
Read with AI
Save time reading this article using your favorite AI tool
Summarize with AI
Never Miss a Trend
Our newsletter is packed with the hottest posts and latest news in social media.

You have many things to do.
Let us help you with social media.
Use our free plan to build momentum for your social media presence.
Or skip ahead and try our paid plan to scale your social media efforts.
P.S. It will be a piece of cake 🍰 with Vista Social
Subscribe to our Newsletter!
To stay updated on the latest and greatest Social Media news. We promise not to spam you!
Enjoyed the Blog?
Hear More on Our Podcast!
Dive deeper into the conversation with industry insights & real stories.